
Part 1: Insani Dimaag - Sabse Bada Loophole (The Human Vulnerability)
Cyber Security ki duniya mein ek bahut mashhoor kahawat hai jo legendary cryptographer Bruce Schneier
ne kahi thi:
"Amateurs hack systems, Professionals hack people."
(Anaadi log computer hack karte hain, lekin Experts insaanon ko hack karte hain.)
The "Unpatchable" Human OS
Zara sochiye: Jab Windows mein koi kami (bug) milti hai, to Microsoft turant ek Update bhejta
hai. Jab Android mein virus ka khatra hota hai, to Google Security Patch release karta hai.
Lekin Insaan (Human Brain) ka koi security update nahi aata. Hamare dimaag mein aaj bhi wahi
purane "Bugs" hain:
- Hum Bharosa (Trust) jaldi karte hain.
- Hum Madad (Help) karna chahte hain.
- Hum Darr (Fear) mein logic bhool jate hain.
Hacker isi "Human Operating System" ko exploit karta hai. Ise technical bhasha mein Social Engineering kehte hain.
The Fortress Analogy (Kile Ki Kahani)
Is concept ko samajhne ke liye ek example lete hain:
Imagine karein ek bohot bada Kila (Fortress) hai.

High Security bhi Human Error ke aage fail hai.
- Uski deewarein 50 feet oonchi hain (Ye aapka Firewall hai).
- Darwaze par armed guards khade hain (Ye aapka Antivirus hai).
- Charon taraf cameras lage hain (Ye IDS/IPS hai).
Koi dushman zabardasti andar nahi ghus sakta. Lekin tabhi ek aadmi "Pizza Delivery Boy" ki dress pehen kar aata
hai aur guard se kehta hai: "Raja Sahab ne Pizza mangaya hai, garam hai, jaldi jane do."
Guard bina check kiye darwaza khol deta hai.
Result: Dushman andar aa gaya. Saari oonchi deewarein aur bandookein dhari ki dhari reh gayi.
Phishing yahi hai. Aap apne computer par duniya ka sabse mehnga security system laga lijiye,
lekin agar aapne khud hacker ko apna password type karke de diya (Pizza Boy ko darwaza khol diya), to koi
software aapko nahi bacha sakta.
Part 2: The Psychology (Hacker ka Jaal)
Hacking sirf computer code ka khel nahi hai, ye dimaag ka khel hai. Hacker jaanta hai ki insaan ka dimaag kaise
kaam karta hai.
Nobel Prize winner Daniel Kahneman ke hisaab se hamare dimaag ke 2 modes hote hain:
- System 1 (Fast & Emotional): Ye bina soche turant faisla leta hai. (Jaise: Kutte ko dekh kar bhagna).
- System 2 (Slow & Logical): Ye soch-vichar kar faisla leta hai. (Jaise: Math problem solve karna).
Phishing ka poora maqsad ye hai ki aapko System 1 mein phansa kar rakha jaye taaki System 2 (Logic) kabhi activate hi na ho paye. Hacker in 6 Psychological Hathiyaron (Triggers) ka use karta hai:
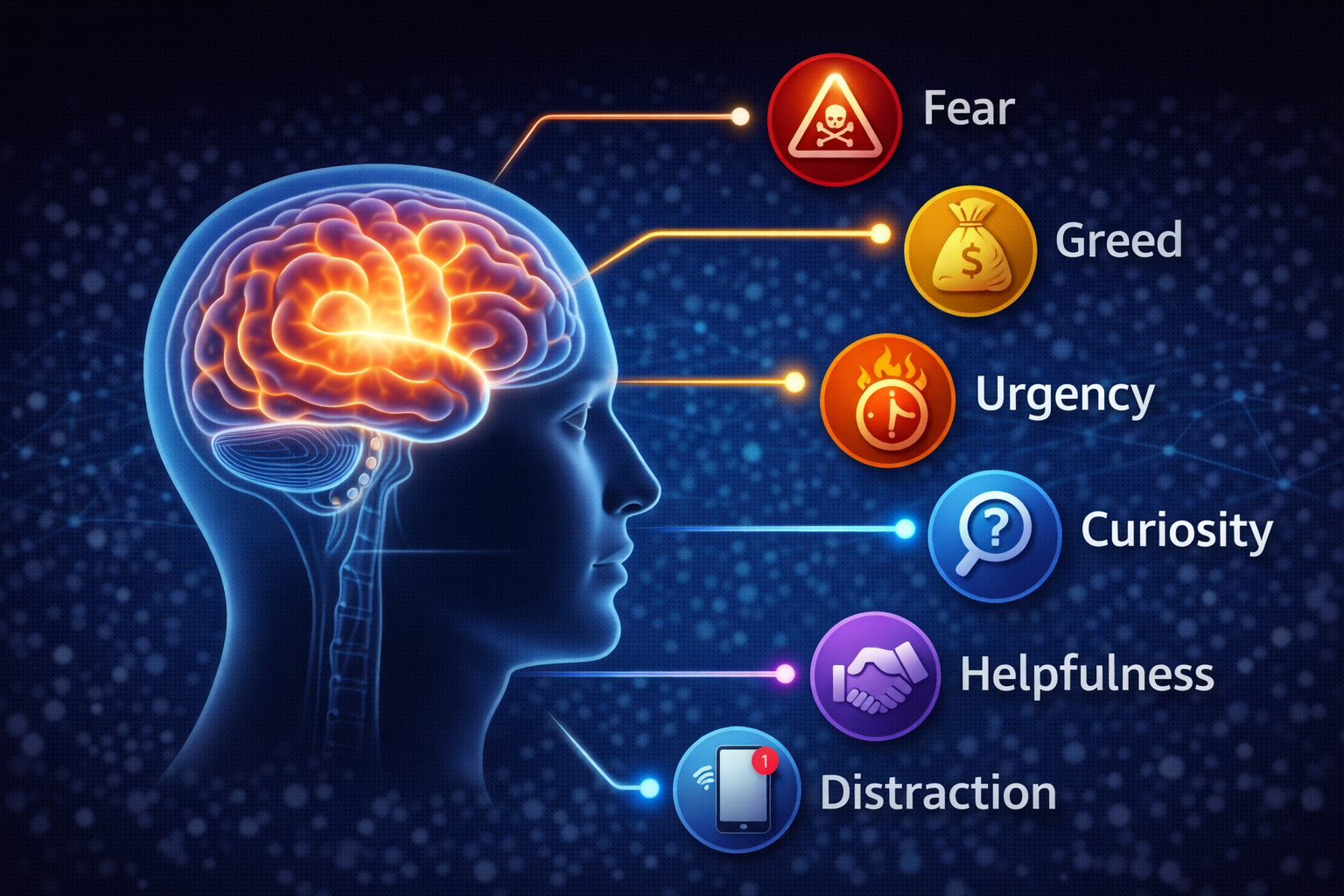
Hacker aapke logic center ko bypass karke emotion ko target karta hai.
1. Fear (Darr - Amygdala Hijack)
Dialog: "Police Case registered against your IP Address!" ya "Bank Account Hacked!"
Science: Jab insaan darta hai, to dimaag ka 'Amygdala' hissa control le leta hai (Fight or
Flight mode). Logic center (Prefrontal Cortex) temporary band ho jata hai.
Result: Aap darr ke maare bina verify kiye link par click kar dete hain taaki "problem
solve" ho jaye.
2. Greed (Lalach - Dopamine Hit)
Dialog: "Crypto Giveaway! Send 1 BTC get 2 BTC back." ya "You won a Lottery!"
Science: Reward ka sunte hi dimaag mein Dopamine release hota hai. Ye wahi
chemical hai jo gambling ya drugs mein nikalta hai. Ye humein "Optimism Bias" deta hai (Humein lagta hai ki
hum lucky hain).
Result: Lalach mein hum sochna band kar dete hain ki "Bina ticket khareede lottery kaise
lagi?"
3. Urgency (Jaldbaazi - Scarcity)
Dialog: "Account will be DELETED in 10 minutes" ya "Last 2 iPhones left at 90% off!"
Science: Ise Loss Aversion kehte hain. Insaan ko kuch paane ki khushi se
zyada kuch khone ka darr hota hai. Hacker aapko sochne ka waqt nahi dena chahta.
Result: Jaldbaazi mein aap URL ya Sender Email check karna bhool jate hain.
4. Authority (Rutba - Obedience)
Dialog: "Message from CEO: Process this invoice immediately" ya "Income Tax Officer
Notice."
Science: Bachpan se humein sikhaya jata hai ki badon ki (Teachers, Parents, Police, Boss)
baat maano. Ise Social Compliance kehte hain. Hum authority ko question karne mein
uncomfortable feel karte hain.
Result: Employee bina verify kiye paise transfer kar deta hai kyunki "Boss ne bola hai."
5. Curiosity (Jigyasa - Information Gap)
Dialog: "Is this you in this video?" ya "Salary Slip of your colleague attached."
Science: Jab dimaag ko adhoori information milti hai (Information Gap), to wo bechain ho
jata hai. Humen us gap ko bharna hi padta hai.
Result: Aap bas ye dekhne ke liye click karte hain ki "Aakhir file mein hai kya?", aur
malware download ho jata hai.
6. Helpfulness (Madad - Social Norm)
Dialog: "Main naya hoon, mera password nahi chal raha, kya aap apna login de sakte hain?"
Science: Hum social animals hain. Humein dusron ki madad karna acha lagta hai. Hacker
"Bechara" bankar aata hai.
Result: Hum kindness dikhane ke chakkar mein security rules tod dete hain.
Part 3: Types of Phishing (The Hacker's Menu)
Phishing ab sirf emails tak seemit nahi hai. Ye har digital platform—SMS, Call, QR Code, Social Media—par aa
chuka hai. Hacker situation ke hisaab se apna "Menu" change karta hai.
Aaiye in sabhi types ko gehraai (Deep Dive) mein samjhein:

1. Bulk Phishing (Spray & Pray)
Concept: Quantity over Quality. Hacker 10 lakh logon ko same email bhejta hai. Use pata hai 99% log ignore karenge, lekin 1% (10,000 log) phans jayenge.
"Netflix: Your payment failed. Account will be suspended."
"Amazon: You won a Gift Card! Claim now."
Pehchan: "Dear Customer" (Naam nahi hoga), aur Grammar mistakes hongi.
2. Spear Phishing (Sateek Nishana)
Concept: Ye personalized attack hai. Hacker pehle Reconnaissance (Jasoosi) karta hai. Wo LinkedIn/Instagram se aapka naam, company, aur job role nikalta hai.
"Hi Rahul, I saw your profile on LinkedIn. Our HR team at Google shortlisted you. Click here to see the offer letter."
Pehchan: Ye asli lagta hai. Verify karne ke liye sender ka email domain check karein.
3. Whaling (CEO Fraud)
Concept: Spear Phishing ka "Big Boss" version. Target sirf High-Profile log hote hain (CEO, CFO, Managers). Maqsad chhota data nahi, balki Millions ka Fund Transfer ya confidential documents hota hai.
"Confidential Legal Notice: Court summons attached. Please review immediately." (CEO darr ke mare open kar lega).
4. Smishing (SMS Phishing)
Concept: SMS open rate emails se zyada hota hai (98%). Hacker short links (bit.ly) use karta hai taaki aap asli URL na dekh paao.
"SBI Alert: Your KY C is pending. Account blocked. Update: bit.ly/sbi-kyc"
"Electricity Bill: Power cut at 9 PM. Pay now: 89xxxx."
5. Vishing (Voice Phishing)
Concept: Voice Modulation aur Caller ID Spoofing ka use. Aapko lagega call Bank ke official number se aa raha hai, par wo hacker hota hai.
Hacker: "Sir, main Mumbai Branch se bol raha hoon. Koi aapke card se 50,000 ki shopping kar raha hai. Block karne ke liye OTP bataiye."
(Darr ke maare victim OTP de deta hai).
6. Quishing (QR Code Phishing)
Concept: Log QR code ko scan karte waqt URL check nahi karte. Hacker parking meters, restaurant menus, ya emails mein malicious QR code chipka dete hain.
Aapne Parking Meter par QR code scan kiya payment ke liye. Payment fake site par gayi aur card details chori ho gayi.
7. Clone Phishing (Duplicate)
Concept: Hacker aapka koi Purana Asli Email leta hai (jo aapko pehle aaya tha), aur uski exact copy banata hai. Bas usme jo attachment ya link thi, use malicious link se replace kar deta hai.
"Resending updated invoice: Sir, pichle email mein link broken tha, please is naye link se invoice download karein."
8. Angler Phishing (Social Media)
Concept: Jab aap Twitter/Insta par kisi brand ko complain karte hain (e.g., "My flight got cancelled!"), hacker turant Fake Customer Care profile se reply karta hai.
Fake AirIndia Support: "So sorry for the delay. DM us your details for instant refund."
(Log gusse mein dhyan nahi dete ki ye official handle nahi hai).
Mobile aur Physical world mein bhi phishing hoti hai.
Part 4: Anatomy of a Phishing Email (The Digital Post-Mortem)
Ek fake email ko kaise pehchanein? Sirf upar-upar se dekhna kaafi nahi hai. Humein email ka
Post-Mortem (Forensic Analysis) karna hoga.
Hacker ki Galtiyan (Red Flags) dhundhne ke liye hum email ko 4 layers mein check karenge:
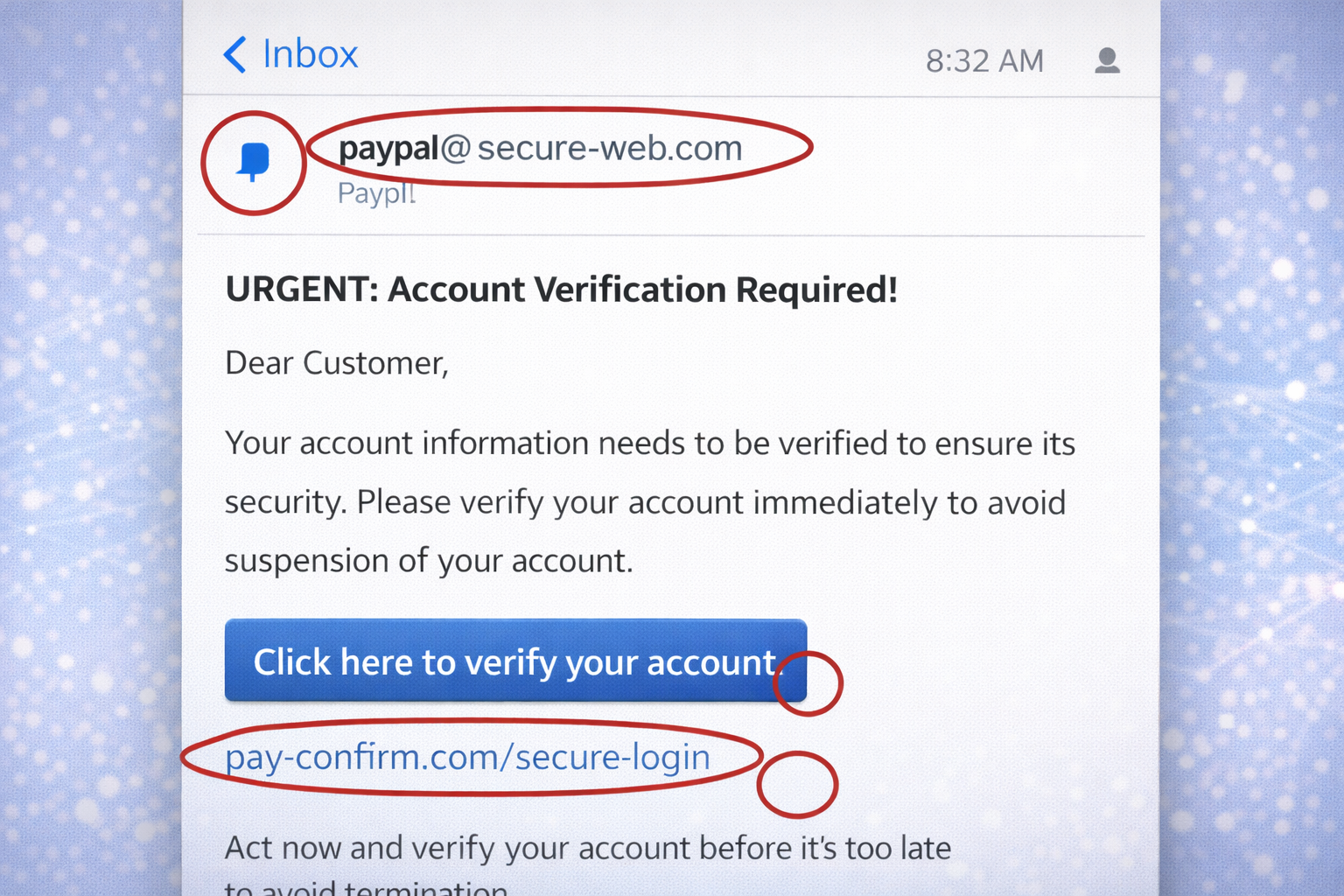
Layer 1: The Identity Crisis (Kaun Bol Raha Hai?)
Sabse pehli nazar "Sender Name" par jati hai, aur wahin hum dhokha kha jate hain.
Layer 2: The Content (Kya Bol Raha Hai?)
Email ki body mein hacker psychological triggers (Darr/Lalach) chipkata hai.
Generic Greeting (Anjaan Aadmi)
Fake: "Dear Customer" ya "Dear Member".
Real: Bank aapka naam jaanta hai: "Dear Harsh Singhal".
Why? Kyunki hacker ne ye mail 1 lakh logon ko bheja hai, wo sabka naam nahi jaanta.
Grammar & Spelling (Jaanbujhkar Galti)
Fake: "Kindley update you're account."
Real: Professional emails mein spelling mistakes nahi hoti.
Why? Hackers jaanbujhkar galti karte hain taaki sirf "kam samajhdar" log hi reply karein (Smart
log ignore kar dein).
Layer 3: The Link Deception (Kahan Le Ja Raha Hai?)
Ye sabse critical part hai. Hacker button ke peeche link chhupa deta hai. Ise check karne ke liye "Hover Test" karein (Mouse ko link ke upar le jayein, click na karein).
Layer 4: Technical Deep Dive (Advanced Users Only)
Agar aap bilkul sure hona chahte hain, to email ka Header check karein (Show Original / View Source).
- Return-Path: Ye wo address hai jahan failed delivery report jati hai. Aksar phishing mein ye 'From' address se alag hota hai.
- SPF/DKIM Fail: Agar header mein
Authentication-Results: faillikha hai, to iska matlab email spoofed hai (Gmail ise warning banner ke saath dikhata hai).
Part 5: Technical Attacks (Advanced Hacks)
Ab hackers sirf "Psychology" par depend nahi karte. Wo aisi advanced technology use karte hain jise pakadna
experts ke liye bhi mushkil hota hai.
Yahan hum un invisible attacks ko decode karenge jo browser ke address bar mein chhupe hote
hain.
1. Homograph Attack (IDN Spoofing)
Computer ke liye 'a' (Latin) aur 'а' (Cyrillic) do alag akshar hain, lekin insaan ki aankhon ke liye wo bilkul
same hain. Hacker iska fayda uthate hain.
Ise IDN (Internationalized Domain Name) Homograph Attack kehte hain.

2. The "Evilginx" Attack (2FA Killer)
Log sochte hain OTP (2FA) unhe bacha lega. Lekin Evilginx2 jaise tools ne game badal diya hai. Ye password nahi, seedha "Login Cookie" churate hain.

Standard Phishing
Hacker fake page banata hai. Aap password dalte hain, wo chori ho jata hai. Lekin OTP nahi milta.
Man-in-the-Middle (MITM) Phishing
Hacker server aur aapke beech "Broker" ban jata hai.
1. Aap Fake Site par OTP dalte hain.
2. Hacker wo OTP turant Real Site par bhejta hai.
3. Real Site login approve karti hai aur Session Cookie deti hai.
4. Hacker wo Cookie chura leta hai aur bina password ke login kar leta hai.
3. HTTPS Lock Myth (Hara Taala Jhoot Hai)
Log sochte hain ki agar URL ke pass 🔒 (Green Lock) hai to site safe hai. Ye sabse bada jhoot
hai!
Lock ka matlab sirf ye hai ki connection Encrypted hai. Iska matlab ye nahi ki samne wala
insaan imandar hai.
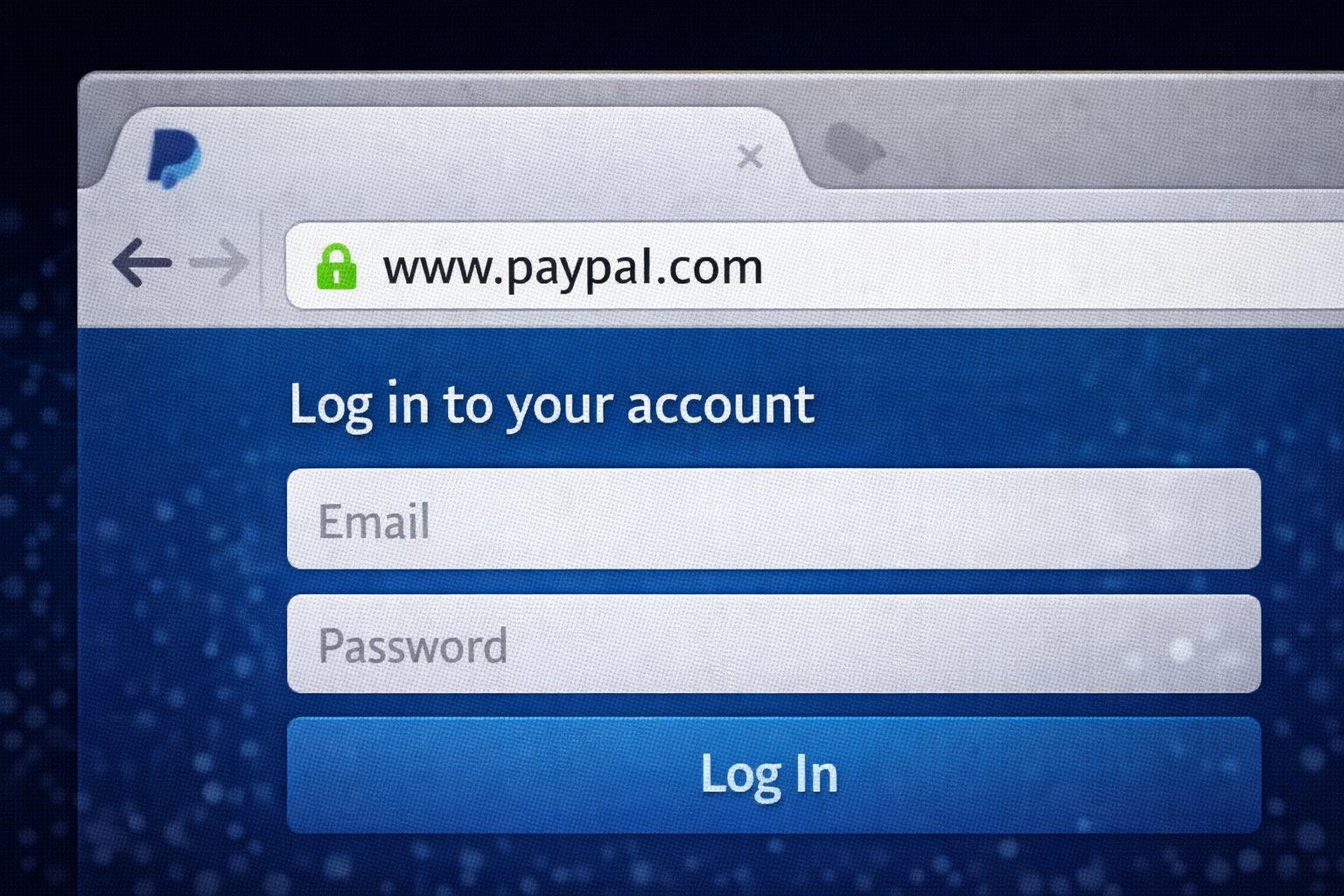
Hacker ke paas bhi 'Secure Lock' ho sakta hai.
Meaning: Aapka password safe tareeke se... Hacker tak ja raha hai.
💻 Tech Corner: The "Right-to-Left" Rule
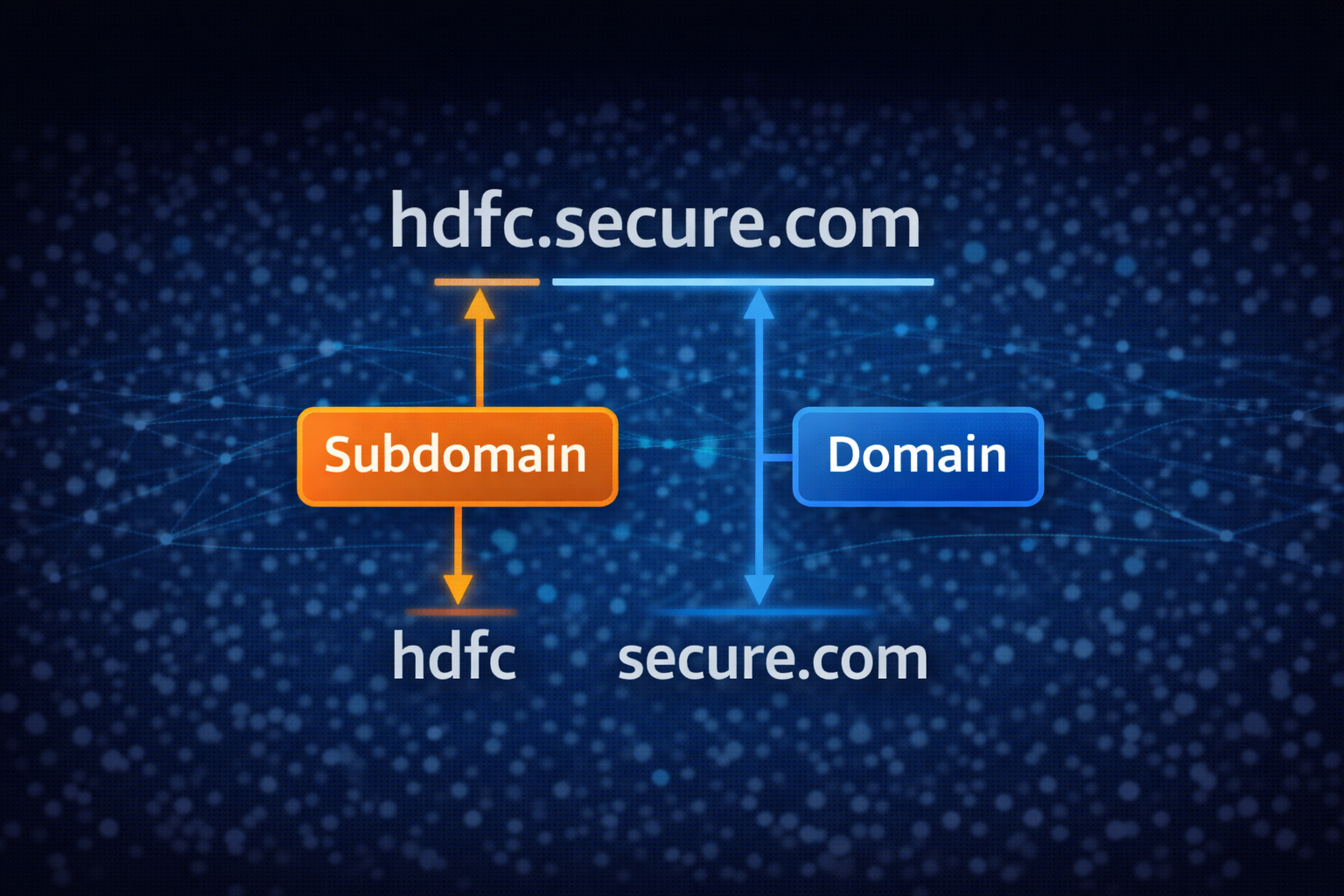
Fake URL pakadne ka ek hi Golden Rule hai: Domain ko hamesha Right-to-Left padhein.
Asli Domain hamesha .com, .in, .org (Top Level Domain) ke theek pehle
hota hai.
Common Obfuscation Tricks:
- Typosquatting:
faceboook.com(Extra 'o') yagogle.com(Missing 'o'). - Combosquatting:
netflix-payment-update.com(Hyphens use karke asli naam jodna). - URL Shorteners:
bit.ly/3x98s(Destination chhupa dena). Hamesha Link Preview tools use karein.
Part 6: Real World Attack - The $100 Million Heist (BEC)
Cyber Security mein sabse mehnge attacks viruses se nahi, emails se hote hain. Ise **BEC (Business Email
Compromise)** kehte hain.
FBI ke mutabiq, BEC scams ne pichle kuch saalon mein companies ka $50 Billion se zyada nuksan
kiya hai. Aaiye duniya ke sabse bade phishing scam ko decode karte hain.
Case Study: The Man Who Conned Google & Facebook
The Villain
Evaldas Rimasauskas (Ek Lithuanian aadmi). Usne koi hacking tool use nahi kiya, koi virus nahi banaya. Usne bas "Email" aur "Paperwork" ka use kiya.
The Victim
Duniya ki sabse Tech-Savvy companies: Google aur Facebook.
Loss: $120 Million (approx ₹1000 Crores).
How He Did It? (Step-by-Step)
Evaldas ne dekha ki Google aur Facebook dono ek Taiwanese company "Quanta Computer" se hardware khareedte hain. Ye unka regular vendor tha.

Why Did They Fail? (The Human Error)
Itni badi companies bewaqoof kaise ban gayi?
- Authority Bias: Invoices professional the aur "Urgent Payment" likha tha. Employees ne seniors se poochna zaroori nahi samjha.
- Lack of Verification: Unhone Vendor ka naam dekha (Quanta), lekin Bank Account Number verify nahi kiya (ki wo Taiwan ka hai ya Latvia ka).
- Siloed Teams: Procurement team aur Finance team ke beech communication gap tha.
Anatomy of a BEC Email (CEO Fraud)
Ek aur common BEC attack hai "CEO Fraud". Isme hacker CEO ban kar Finance Head ko mail karta hai.
From: Sundar Pichai <ceo-google-corp@email.com>
To: Chief Financial Officer
Subject: Urgent Wire Transfer - Confidential Acquisition
Hi,
Hum ek secret company acquire karne wale hain. Ye deal abhi public nahi honi chahiye. Mujhe agle 1 ghante mein $5 Million is attached account par transfer chahiye.
Main abhi meeting mein hoon, call mat karna. Just process it ASAP.
Regards,
Sundar
The Trap
1. Urgency: "1 ghante mein chahiye."
2. Secrecy: "Secret deal hai, kisi ko mat batana."
3. Availability: "Meeting mein hoon, call mat karna" (Taaki verify na kar sake).
The Defense (Bachav)
"Out-of-Band Verification"
Agar email aaya hai, to reply mat karo. Phone uthao aur call karo.
Poocho: "Sir, kya aapne ye mail bheja hai?" 99% scams yahin pakde jate hain.
Part 7: The Ultimate Defense Shield (Armor Up)
Phishing se bachne ke liye sirf "Dhyaan rakhna" kaafi nahi hai. Insaan galti karega hi. Humein technology ka use karke ek aisa Kavach (Shield) banana hai jise hacker tod na sake.
1. MFA / 2FA (The Brahmastra)
Concept: Agar hacker aapka password chura bhi le, tab bhi wo login nahi kar payega kyunki uske paas "Second Key" nahi hai.
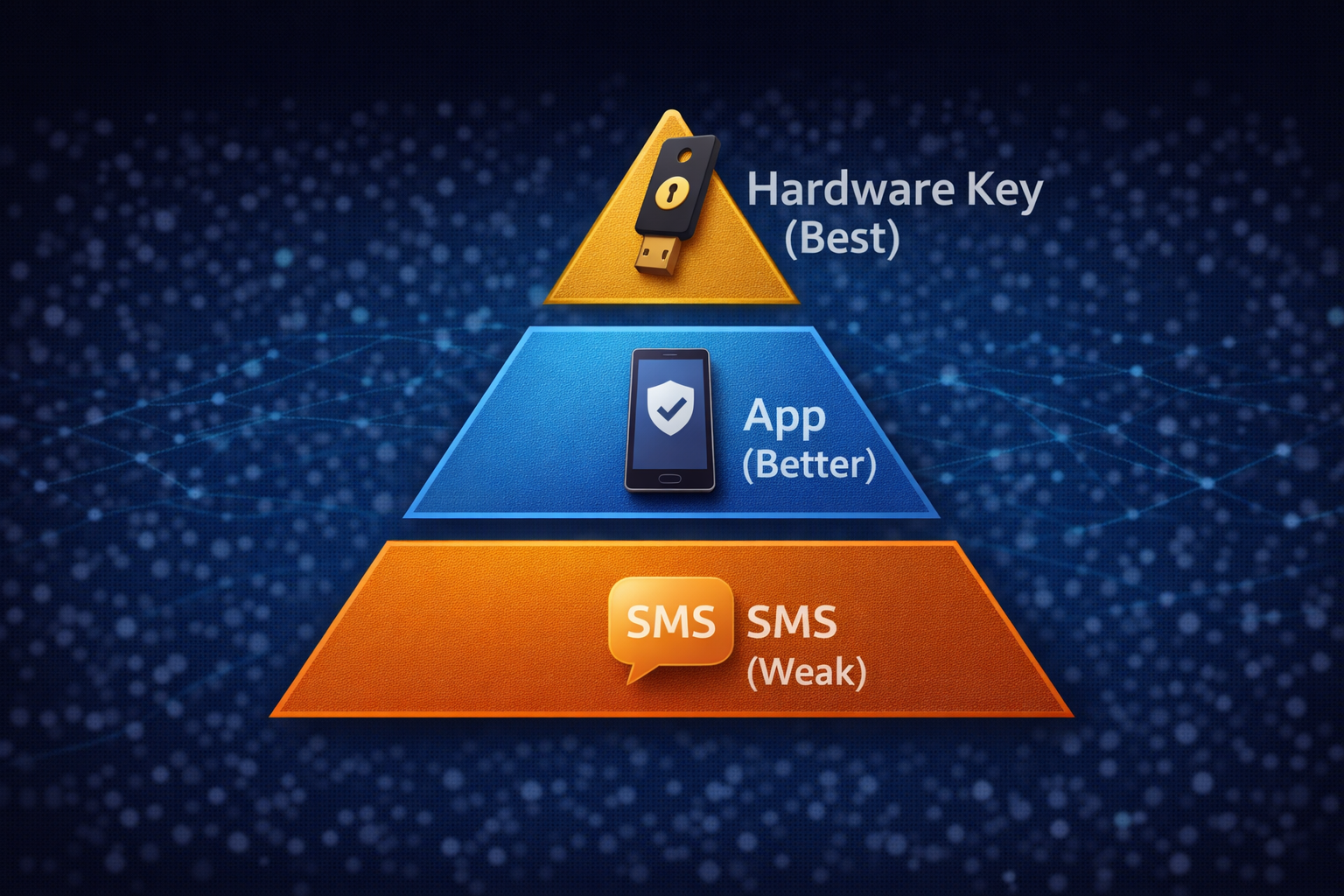
- ❌ SMS OTP: Weakest. (SIM Swapping se hack ho sakta hai).
- ✅ Authenticator App: Better. (Google/Microsoft Auth). Ye offline kaam karta hai.
- 🚀 Hardware Key (YubiKey): Ultimate. (USB key jo laptop mein lagani padti hai). Evilginx bhi ise bypass nahi kar sakta.
2. Password Manager (The Phishing Detector)
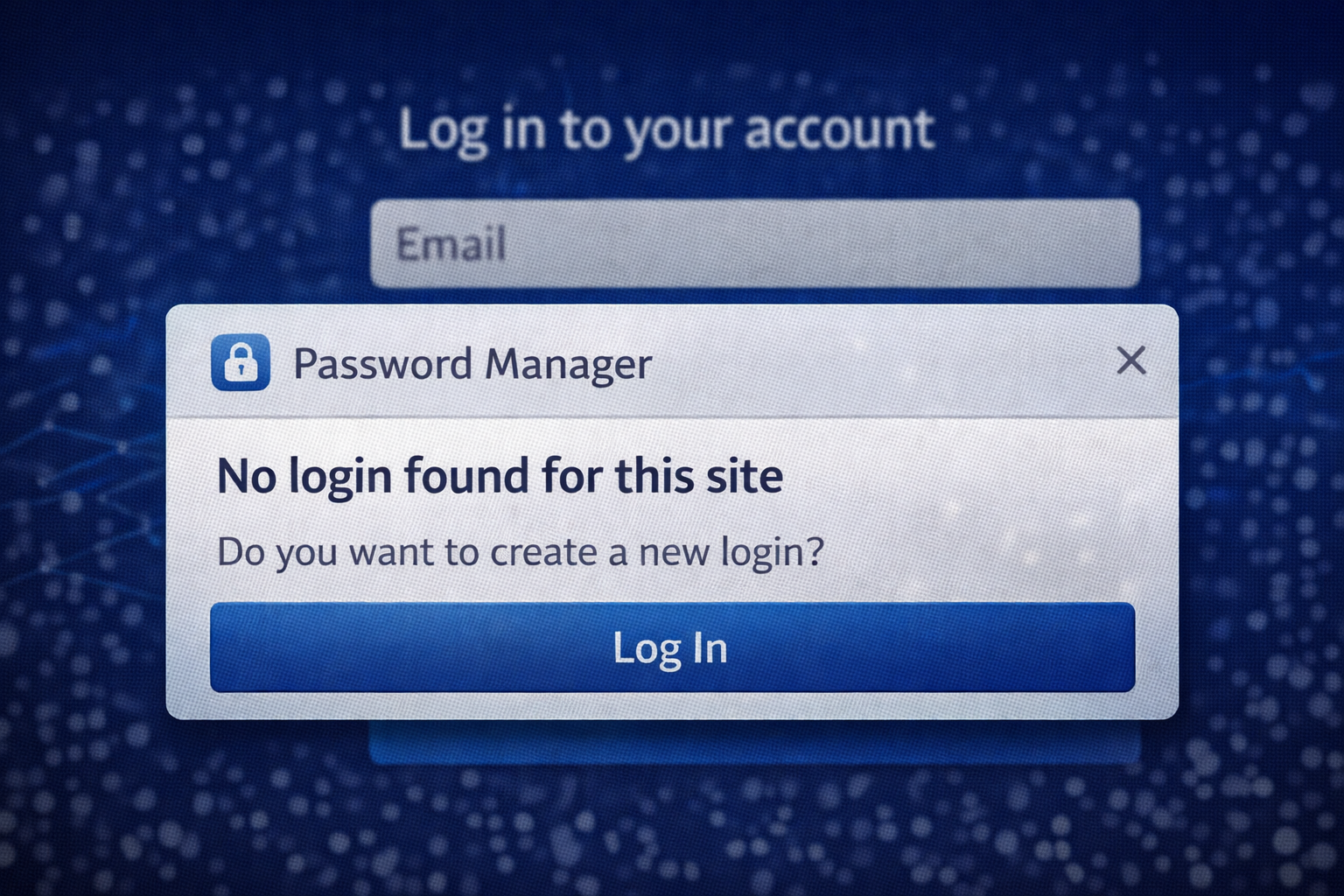
Concept: Log ise sirf password store karne ke liye use karte hain, lekin ye Best Phishing Detector bhi hai.
Password Manager (jaise Bitwarden/1Password) sirf tabhi password Auto-fill karega jab URL
google.com se exact match hoga.
Agar URL gooogle.com (Fake) hai, to wo password fill nahi karega.
Rule: Agar Auto-fill nahi hua, to manual type mat karo! Site fake hai.
3. Email Protocols (Business Shield)
Concept: Agar aap company chalate hain, to ye 3 records apne DNS mein zaroor lagayein. Ye hacker ko aapke naam se fake mail bhejne se rokte hain.
- SPF (Sender Policy Framework): Ek List jo batati hai ki "Kaunsi IP address mere naam se mail bhej sakti hai."
- DKIM (DomainKeys Identified Mail): Ek Digital Seal. Agar mail raste mein edit hua, to seal toot jayegi.
- DMARC: Ye instruction hai: "Agar SPF ya DKIM fail ho jaye, to us mail ko Spam mein daal do ya Reject kar do."

4. Browser Extensions (Bonus)
Concept: Kuch free extensions hain jo malicious sites ka database rakhte hain.
- Netcraft Extension: Ye nayi phishing sites ko turant block karta hai.
- uBlock Origin: Sirf ads nahi, malicious domains bhi block karta hai.
📝 Final Assessment - Are You Hack-Proof?
Chaliye dekhte hain ki aapne kitna seekha. Agar aap in 10 mein se 8 sahi javab dete hain, to aap safe hain.
Q1: "Urgent! Account Blocked in 10 mins" - Ye hacker kis emotion ka use kar raha hai?
Q2: Is URL mein asli website kaunsi hai: `https://google-login.secure-update.com`?
Q3: Browser address bar mein `xn--80ak6aa92e.com` dikh raha hai. Ye kya hai?
Q4: Hacker CEO ban kar Finance Team ko "Urgent Fund Transfer" ka mail karta hai. Ise kya kehte hain?
Q5: Kya "Green Lock" (HTTPS) hone ka matlab ye hai ki website 100% Safe hai?
Q6: Evilginx attack (MITM) mein hacker kya churata hai jisse wo 2FA (OTP) ko bypass kar sake?
Q7: Password Manager aapko phishing se kaise bachata hai?
Q8: Sabse SURAKSHIT (Secure) MFA method kaunsa hai?
Q9: Agar Email Header mein `SPF: Fail` likha ho, to iska kya matlab hai?
Q10: Agar aapko apne CEO se "Urgent Money" ka mail aaye, to sabse pehle kya karna chahiye?
📊 Score Interpretation
8-10 Correct: 🛡️ Cyber Ninja! Aapko bewakoof banana namumkin hai.
5-7 Correct: ⚠️ Cautious User. Aap basics jante hain, lekin Advanced Attacks
(Evilginx, Punycode) mein phans sakte hain. Dobara padhein.
0-4 Correct: 🚨 High Risk! Aap hackers ke liye "Easy Target" hain. Please is
blog ko dobara dhyan se padhein.