
Part 1: Hacker Kaun Hai? (Myth vs Reality)
Movies mein hum dekhte hain ki ek ladka hoodie pehen kar andhere kamre mein tezi se typing karta hai aur 2
second mein "ACCESS GRANTED" aa jata hai. Ye jhoot hai.
Asliyat mein, Hacker wo insaan hai jo system ko itni gehraai se samajhta hai ki wo use aise
kaam karwa sake jiske liye wo bana hi nahi tha.
Hacking illegal nahi hai. Bina permission ke hack karna illegal hai. Agar aap permission lekar
hack karte hain, to aap Security Expert hain. Agar bina permission ke karte hain, to Criminal.
Part 2: The Hat Spectrum (Hacker Types)

Hackers ko unki niyat (intention) ke hisaab se alag-alag rang (hats) diye gaye hain.
🛡️ White Hat (The Good Guys)
Alias: Ethical Hackers / Security Researchers
Intent: Protection
Ye companies se permission lekar unhe hack karte hain taaki unki kamiyan (bugs) dhundh kar fix kar
sakein. Inhein is kaam ke paise milte hain.
💀 Black Hat (The Bad Guys)
Alias: Crackers / Threat Actors
Intent: Destruction / Money
Ye bina permission hack karte hain data churane, destroy karne ya ransom (phirauti) maangne ke liye. Ye
criminals hain.
🎭 Grey Hat (The Confused Guys)
Alias: Vigilantes
Intent: Curiosity / Fame
Ye bina permission hack karte hain (Illegal), lekin nuksan nahi pahunchate. Ye company ko batate hain
"Dekho maine tumhe hack kar liya".
Other Dangerous Categories
- Script Kiddies (Green Hat): Beginners jo dusron ke banaye tools (scripts) use karte hain bina unhe samjhe. Ye sabse zyada shor machate hain lekin knowledge kam hoti hai.
- Hacktivists: Jo political reason ke liye hack karte hain (Ex: Anonymous Group). Ye corruption expose karne ke liye websites down karte hain.
- State-Sponsored Hackers: Jine governments hire karti hai dusre deshon par cyber attack karne ke liye (Cyber Warfare). Inke paas unlimited budget hota hai.
Part 3: Corporate Warfare (Red vs Blue)

Companies mein "Hacker" word use nahi hota. Wahan Teams hoti hain jo war-games khelti hain taaki company secure rahe.
🔴 Red Team (Attackers)
Role: Offensive Security
Ye hackers ki tarah act karte hain. Inka kaam hai bina bataye company par attack karna aur security
todna.
Mindset: "Main kaise ghus sakta hoon?"
🔵 Blue Team (Defenders)
Role: Defensive Security
Ye guards hote hain. Inka kaam hai Red Team ke attacks ko detect karna aur rokna.
Mindset: "Main inhe kaise rok sakta hoon?"
🟣 Purple Team (Collaborators)
Role: Analysis
Ye ensure karte hain ki Red aur Blue teams aapas mein baat karein aur findings share karein taaki
company ki security improve ho.
Part 4: The Cyber Kill Chain (Hacking Kaise Hoti Hai?)
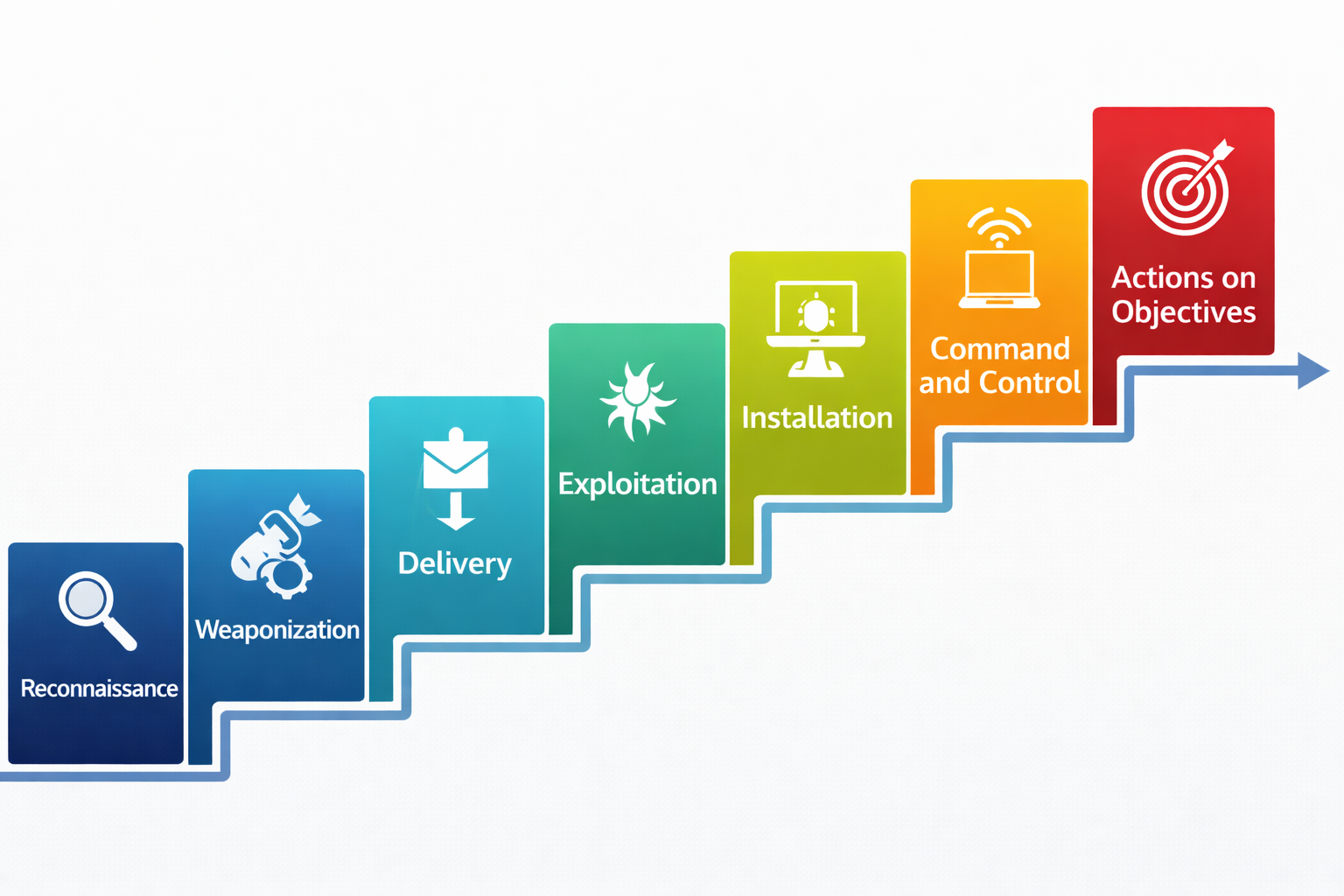
Lockheed Martin ne ek model banaya tha ki ek successful hack ke 7 steps hote hain. Agar defender ne kisi bhi step par chain tod di, to attack fail ho jayega.
Part 5: Bug Bounty (Legal Hacking for Money)

Kya aap jaante hain ki aap Google, Facebook, aur Apple ko hack karke legally Crores kama sakte hain? Ise Bug Bounty Hunting kehte hain.
Process Kya Hai?
- Sign Up: HackerOne ya Bugcrowd jaise platforms par register karein.
- Choose Target: Wahan companies list hoti hain (Ex: Uber, Airbnb) jo allow karti hain testing.
- Find Bug: Unki website/app mein security kami dhundhein (Ex: XSS, SQLi).
- Report: Ek detailed report likh kar company ko bhejein.
- Get Paid: Agar bug valid hua, to wo aapko paise (Bounty) denge aur Hall of Fame mein naam.
💻 Tech Corner: The Hacker's Toolkit

Ek hacker ke bag mein kya hota hai? Sirf laptop nahi, kuch hardware gadgets bhi hote hain.
Rubber Ducky (USB)
Ye Pen Drive jaisa dikhta hai, lekin computer mein lagate hi ye keyboard ban jata hai aur 1 second mein virus type kar deta hai.
WiFi Pineapple
Ye router jaisa dikhta hai. Ye aas-paas ke logon ko fake WiFi signal deta hai taaki log isse connect hon aur hacker unka data dekh sake.
Flipper Zero
Ek chhota sa toy jaisa device jo radio signals copy kar sakta hai—TV band karna, car unlock karna, RFID cards clone karna.
Languages for Hackers
📝 Final Assessment
Q1: Ek hacker jo company ki permission lekar hack karta hai?
Q2: Cyber Kill Chain ka pehla step kya hai?
Q3: Kaunsi team attackers (hackers) ka role play karti hai?
Q4: Script Kiddie kaun hota hai?